ProtonVPN on pfsense 2.6.x with WireGuard
Note: this document explains configuring a standard ProtonVPN server, not Secure Core. Though configuring that is probably similar.
In ProtonVPN WireGuard settings, select platform Router, your server of choice, and any optional settings. Click Create when you're done.
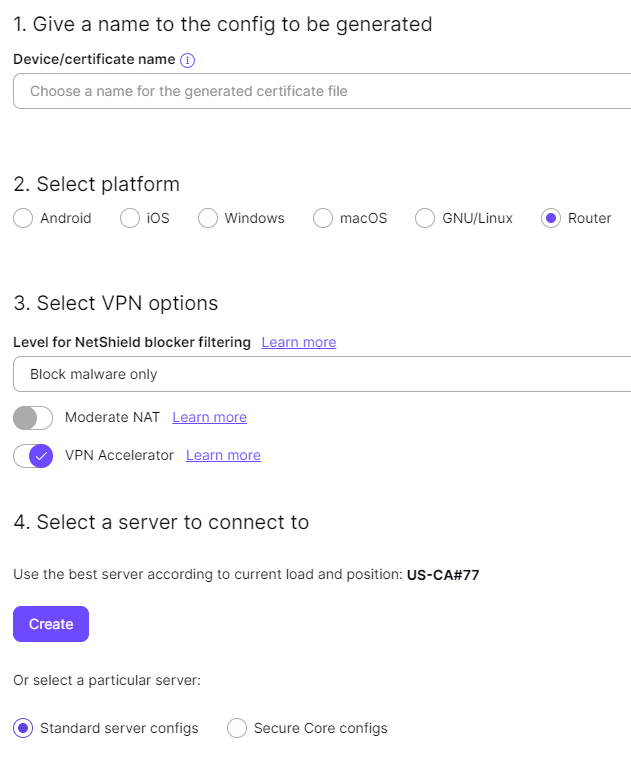
You'll see some configuration details generated at the top that looks like this:
[Interface]
# Key for ProtonVPN WireGuard
# NetShield = 1
# Moderate NAT = off
# VPN Accelerator = on
PrivateKey = <redacted>
Address = <redacted>/32
DNS = <redacted>
[Peer]
# US-CA#77
PublicKey = <redacted>
AllowedIPs = 0.0.0.0/0
Endpoint = <endpoint_ip_of_US-CA#77>:51820
In pfsense, go to VPN > WireGuard.
Click Add Tunnel.
Now you should be in a tunnel configuration screen.
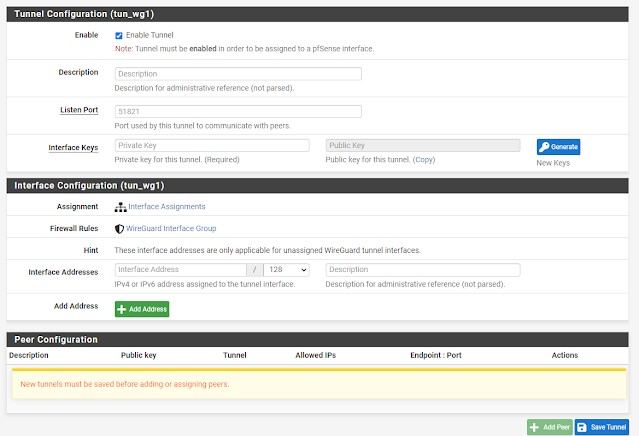
Give a Description like ProtonVPN WireGuard
Listen Port default is 51820
Copy and paste PrivateKey from ProtonVPN config [Interface] to Interface Keys: Private Key
Click Save Tunnel
Now let's add a Peer for the tunnel
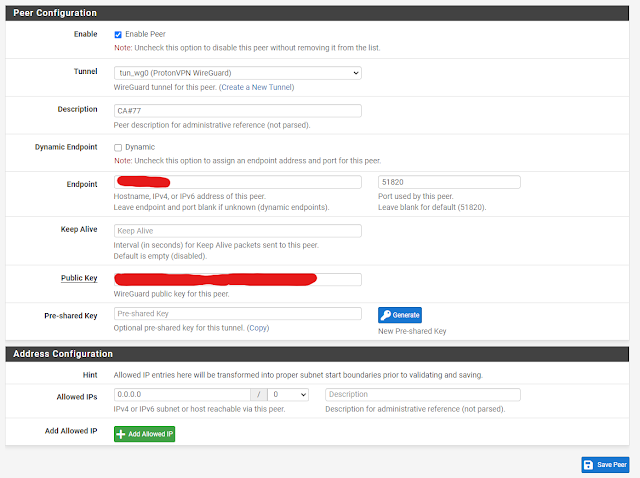
Description: give it something that makes sense to you, like the name of the ProtonVPN server
Dynamic Endpoint: uncheck
Endpoint: Endpoint IP from the ProtonVPN config [Peer]
Public Key: PublicKey from the ProtonVPN config [Peer]
Allowed IPs: 0.0.0.0/0 (this means any traffic is allowed)
Go to Interfaces > Interface Assignments and select Available network ports your newly created tun_wg0 or similar and then click Add
Click the new interface (OPT#) and enter:
Description: something like ProtonVPNWireGuard
IPv4 Configuration Type: Static IPv4
IPv4 Address: the Address in ProtonVPN config [Interface]
IPv4 Upstream gateway: click Add a new gateway and just click Add. You can review settings in System > Routing
Save
Go to Firewall > Rules and set up the rule for the interfaces you want its devices to be always on VPN, such as LAN, WIFI, GUEST, etc..
The rule might look like this

where VPN_Only is my alias for all networks/IPs I want VPN on, any to any traffic, and ProtonVPNWireGuardGW is the Gateway the rule uses to route
Make sure this rule is BELOW a rule you DON'T want traffic to route to VPN i.e. using default gateway e.g.

Similarly you can make rules above this for pfBlocker aliases to allow Netflix traffic to go over the default interface. That may be a future post.
Go to System > Routing > Gateways, and give it a Monitor IP of an internet IP, such as Google's DNS server 8.8.8.8 or 8.8.4.4
This will allow you to monitor the status of the interface. By default, it would just ping itself which is obviously 100% uptime. You want to see something like this in the dashboard
Done.